
Security is undoubtedly essential to the product lifecycle management (PLM) community. Manufacturing companies are always fearful of losing their precious intellectual assets. Thus, data protection is always a high-priority when evaluating PLM systems.
Secure PLM software is the requirement of every business nowadays. Any Oracle Agile PLM professional can easily understand the need to secure the PLM system and assess its security regularly. Securing information in a PLM system is considered to be a multi-dimensional problem.
In this article we will discuss the importance of secure product lifecycle management software. This article gives a comprehensive overview of Agile PLM security and secure PLM.
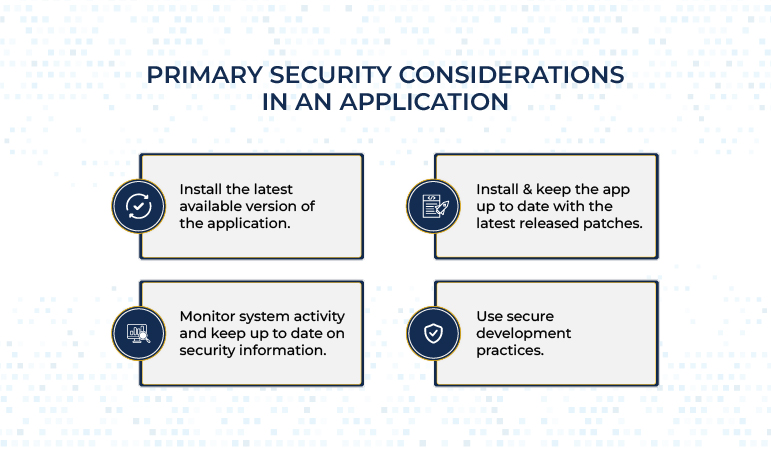
Primary considerations for security in an application
Here’s a list of actions required to keep any application secure.
- Install the latest available version of the application.
- Install and keep the application up to date with the latest released patches.
- Monitor system activity and keep up to date on security information.
- Use secure development practices.
Security in Oracle Agile PLM
Oracle Agile PLM is similar to other IT systems. They all require security to safeguard the interests of the end user. Since every other organization is becoming globalized, it carries a lot of sensitive customer and company information. This information is stored across different locations and requires immediate security.
With reference to the agile product lifecycle management, businesses should implement maximum security measures that have access control models to ensure security.
These models drive compliance to standards, including ITAR or International Traffic in Arms Regulations and EAR or Export Administration Regulations. PLM access control of such nature should be implemented for user criteria, privileges, and roles within the system.
Here are some principles that are necessary for ensuring PLM security. Let’s see what are the principles for PLM security and how integral are they for PLM access and overall security:
Keeping Agile PLM up to data
It is a good security practice to make sure that the Agile PLM system is always the most current and updated version. Cloud-based PLM security involves regularly checking the Updates Page for any new releases, patches, and updates to existing and new Agile PLM, Agile product lifecycle management versions.
Network Access Restrictions
You should place both the PLM application and the database behind a firewall to ensure access security. Moreover, it would be best to set an additional firewall between the application server and the database.
This is where Oracle agile property shines. This ensures that the system access is restricted to known network routes only and is ready to be monitored or restricted if needed. Oracle PLM has always put security paramount.
However, an alternate is configuring the TNS listener valid node checking feature or using a hardware or software VPN (or both) if needed. This step also secures Oracle product lifecycle management.
Principle of Least Privilege
The principle of least privilege in oracle agile PLM states that any user with access to the PLM system should have the minimum number of privileges needed to perform their job. No extra privilege should be granted, not even one. PLM overview also stands by the same notion.
Over-ambitious granting of privileges/roles to get work done quickly always leaves the system open for abuse. Thus, it almost always becomes a major concern in an organization’s PLM usage lifecycle.
Therefore, for secure PLM, you should undertake periodic reviews of privileges to ensure that users are assigned only the relevant privileges.
System Monitoring
Any PLM systes and security overview of Oracle Agile PLM depends on its security protocols, the system configuration, and system monitoring. Agile PLM and Oracle Agile PLM provide its administrators with audit advice for regularly monitoring and reviewing audit records.
Resources to be considered for Security
We have listed some examples of sensitive data that is stored in Agile PLM. For Oracle Agile PLM there has to be adequate protection to ensure security.
- Product data, such as part numbers, other attributes, and product files. PLM overview suggests every aspect of Oracle Agile PLM requires consideration for maximum security.
- Quality documents and quality processes
- Project plans and execution details
- Project cost
- Product compliance documentation and process details
Securing data and predicting potential failures
There is a need to secure data and predict potential failures or breaches in securing strategic resources when it comes to Oracle Agile PLM. For example, there could be a need to analyze workflow statuses in Oracle PLM to determine who needs access to which data at what stage of the product lifecycle management.
Similarly, you might need to protect the data of one subscriber of the application from others while giving complete access to someone from the management. This is the extent of security in Oracle Agile PLM.
Sometimes, the failure to secure data is nothing more than an inconvenience in PLM access. However, a simple fault in the security setup often causes catastrophic damage to you or your customers. Therefore, it is crucial to understand the security ramifications of each resource to ensure its protection. This is why we emphasize on cloud-based PLM security.
Best Practices for Securely Configuring Agile PLM
Password Policy
It is recommended that you define a set of rules determining how passwords are used to maintain security in Oracle Agile PLM. Here are some rules in agile product lifecycle management that you should consider:
- The maximum length of a password should be valid.
- The minimum number of characters in a password.
- The number of maximum logins tries.
Authentication
Similarly, robust authentication processes serve as a bulwark against security breaches in Oracle agile. They enable only permitted individuals to get access to the system and data. All these are necessary protocols and procedures in Oracle Agile PLM.
LDAPS (Lightweight Directory Access Protocol Secure)
- Oracle Internet Directory Server.
- Microsoft Active Directory Server.
- Sun Java System Directory Server.
- Oracle Virtual Directory.
SSO (Single Sign-On)
- SSO integrates with a centralized security management system.
- Having a centralized system also helps improve user productivity in oracle agile PLM.
- Agile PLM system allows setting up Process Extensions to access the Agile server without the user having to re-authenticate. It passes encrypted SSO tokens that process the extensions and submit them back to the Agile server.
Database authentication configurations
- An alternative to SSO and LDAP security.
- No centralized management and relatively easier to manage.
Custom MFA
Employing multi-factor authentication (MFA) software is a straightforward and effective way to guarantee that the users accessing your systems are who they say they are. Xavor’s Agile multi-factor authentication solution allows you to introduce another layer of security when accessing Agile. Xavor takes security up a notch in Oracle Agile PLM.
Here’s how it works. Upon login, a user must submit an access code emailed to their registered email address.
Seamless integration with existing and future agile users removes the burden on your IT team to manage user accounts. Moreover, Xavor’s Agile MFA enables plm integration with existing third-party MFA providers.
Configuring & Using Access Control
User access is primarily divided into two processes.
- Allowing only certain users access to the process and data.
- Allowing only need-based access to specified users, limiting or restricting any excessive rights to the process or data.
Security Audit in Agile PLM
Agile PLM and Oracle product lifecycle management allow you to audit the system by utilizing some of the following resources.
User Monitor
- Displays users currently accessing the system.
- Displays user details such as name, ID, host, and usage time.
History Tab
- Displays any action performed for an item, e.g., creation, save as, send, print, modify, etc.
- Displays administrator actions for all configuration actions.
Log Files
- Provide customizable logging controls to get in-depth Security related information.
- Generate log files for the application and WebLogic.
SSL Configuration Setup
Oracle Agile PLM supports configuring SSL on our client side to secure sensitive cookies. Moreover, it enables you to route the data/information between clients and from client to server in an encrypted, secure way.
SSL can be set up in Oracle Agile PLM on the following:
- Web Services
- WebLogic Server
- AutoVue Server
- Tomcat Server
Xavor’s Security Evaluation Approach
Xavor’s experienced Agile PLM team provides security assessments to identify any vulnerabilities in your Agile PLM servers and its security model.
Moreover, we have many years of experience serving and managing PLM customers, which puts us in a unique position to assist them in their PLM system’s security evaluation. We employ modern tools and resources for secure PLM software to identify risks and advise improvements.
Conclusion
At the cost of repetition, we must emphasize the importance of Security in oracle agile PLM systems. Thus, there is an obvious need to adopt best practices and periodically assess PLM security in secure product lifecycle management software.
We live in a globalized manufacturing world where PLM systems play a vital role. Therefore, identifying and rectifying security weaknesses in the PLM server and Agile PLM’s internal security model is crucial and it makes PLM security top notch.
Ready to explore our services of Oracle Agile PLM.? Drop us a line at [email protected] to book a free consultation session!
