In today’s digital landscape, security is of paramount importance, especially when it comes to web applications. React, being a popular JavaScript library for building user interfaces, requires careful consideration of authentication and authorization mechanisms to protect sensitive user data and ensure a secure application environment.
Let’s explore the concepts of authentication and authorization in React applications and discuss the implementation of best security practices for your application. But first, let’s talk about security vulnerabilities in React applications.
Security Vulnerabilities in React Applications
As business data becomes ever more important in a company’s success, keeping it secure is becoming even more vital. Today’s technology landscape is teeming with different technologies, tools, programming languages, and so on. This wide array of options to choose from makes it crucial that you’re aware of the potential vulnerabilities of a certain tool, programming language, or technology.
React is popular for being fast and easy to use. But this may also mean that it’s easy for you to forget about its potential risks. It does not possess strong default security settings, which makes it vulnerable to cyber threats. Privacy regulation violations are a real possibility if you don’t take proactive steps to mitigate security concerns.
Moreover, the private and financial information of app users is always at risk given the immense volumes of data applications share each day. Therefore, you must make all efforts to ensure the security practices of your application.
Common Security Threats to React Applications
- XSS (Cross-Site Scripting): A security threat where malicious scripts are injected into a web application, either through user input or by manipulating the application’s output. There are two types of XSS attacks: reflected and stored. Reflected XSS refers to the immediate execution of the injected script, while stored XSS is when the script is permanently stored and executed when other users access the affected page.
- Broken Authentication: This threat occurs when the authentication mechanism of a web application development is flawed, allowing attackers to bypass or compromise user authentication, and gain unauthorized access to sensitive data or functionalities.
- SQL Injection: An attack technique where malicious SQL queries are injected into an application’s database query, enabling unauthorized access or manipulation of the database. Attackers can extract, modify, or delete data, potentially leading to data breaches or system compromise.
- XML External Entity (XXE) Attack: In this type of attack, an attacker exploits vulnerabilities in XML parsers to access and manipulate external entities or files. XXE attacks can lead to information disclosure, denial of service, or even remote code execution.
- Zip Slip: A security vulnerability that occurs when an application insecurely handles zip files. Attackers can use specially crafted zip archives to overwrite or extract files to unintended directories, potentially leading to arbitrary file disclosure, path traversal, or remote code execution.
- Arbitrary Code Execution: This threat involves the unauthorized execution of arbitrary code or commands on a system. Attackers exploit vulnerabilities in an application to execute malicious code, gaining full control over the affected system, which can lead to data breaches, system compromise, or unauthorized operations.
Best Practices for Authentication
Authentication refers to the process of verifying the identity of users, ensuring that they are who they claim to be. You can achieve this by requesting users to provide credentials such as usernames and passwords. In a React application, you can implement authentication using various methods, including traditional session-based authentication or token-based authentication.
Session-based authentication involves the server creating a session for each authenticated user and storing session information on the server side. The server generates a session ID, which is sent to the client as a cookie. The client includes this session ID in subsequent requests, allowing the server to identify and authenticate the user.
Token-based authentication relies on the use of tokens, which are typically JSON Web Tokens (JWTs). When a user logs in, the server generates a JWT containing user information and signs it using a secret key. This token is then sent to the client, which stores it in local storage or a cookie. Subsequent requests from the client include this token, allowing the server to verify the user’s identity.
How to Implement Authentication in a React App?
To implement authentication in a React application, React developers can utilize popular libraries such as `react-router` and `react-redux`. These libraries provide essential tools for managing authentication-related components and states.
When a user logs in, the system updates the authentication state, and the application is able to render different components depending on the user’s authentication status. The web application can create private routes to limit access to specific parts of the application exclusively to authenticated users.
Best Practices for Authorization
Authorization deals with determining what actions a user is allowed to perform within the application. While authentication ensures that a user is logged in, authorization defines the specific permissions and privileges associated with that user’s role or level of access.
Implementing authorization in a React application often involves defining roles or permissions and checking them against the user’s authentication data. You can do this by storing role information in the authentication token or by making additional server requests to retrieve the user’s roles or permissions.
React application security can utilize role-based authorization by conditionally rendering components or features based on the user’s role. For example, an administrator may have access to certain administrative features that a regular user does not. By checking the user’s role, the application can control the visibility and functionality of specific components accordingly.
Security Best Practices for React Applications
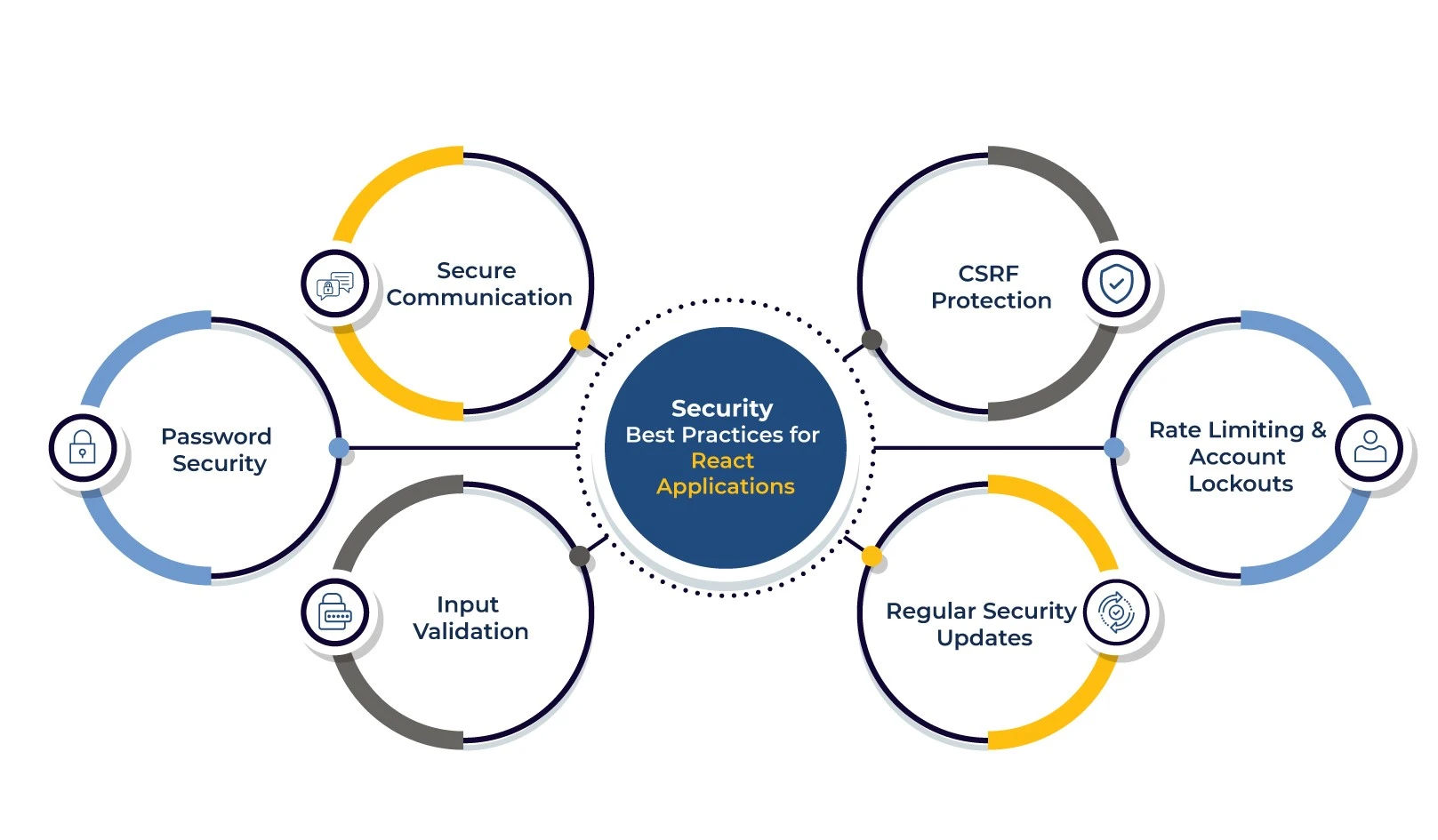
When implementing security features in React applications, there are a few best practices to consider:
- Secure Communication: Ensure that all communication between the client and server is performed over HTTPS to encrypt the data and prevent unauthorized access.
- Input Validation: Validate and sanitize user input on both the client and server sides to mitigate the risk of cross-site scripting (XSS) attacks and other forms of input-based vulnerabilities.
- Password Security: Implement strong password policies, including password complexity requirements, password hashing, and salting on the server side. Avoid storing passwords in plain text or using weak encryption methods.
- Cross-Site Request Forgery (CSRF) Protection: Implement CSRF protection mechanisms, such as using CSRF tokens, to prevent unauthorized requests from malicious websites.
- Rate Limiting and Account Lockouts: Implement rate limiting to prevent brute-force attacks and consider implementing account lockouts after multiple failed login attempts to protect against unauthorized access.
- Regular Security Updates: Stay up to date with security patches and updates for the libraries and dependencies used in your React application to address any known vulnerabilities.
By following these tips, you can help to keep your React applications secure.
Conclusion
Authentication and authorization are essential security features that all React applications should implement. By implementing these features, you can help to protect your applications from a variety of attacks. In addition to authentication and authorization, there are a number of other security features that you should consider implementing in your React applications. By following the tips in this article, you can enhance React application security.
For more information on keeping your web applications secure, reach out to us at [email protected].

